Incentiv takes a familiar model, Proof-of-Work, and evolves it into something fundamentally more aligned with real-world usage and economic value. Old PoW systems rewarded miners with static, inflationary payouts. Incentiv replaces this with a dynamic, demand-coupled security model that grows stronger as the network becomes more useful.
It’s not simply PoW. It’s PoW redesigned for an adaptive, sustainable, human-centric ecosystem.
Why We Chose Proof-of-Work
Proof-of-Work remains the only consensus mechanism that is truly open to anyone. No staking requirements. No minimum token balance. No validator cartels.Just a GPU, electricity, and the willingness to contribute. PoW offers something uniquely powerful: Neutrality — Security rooted in physics, not wealth.
Accessibility — Anyone can mine; no capital gatekeeping.
Predictability — Deterministic validation and simple rules.
Global decentralization — Broad participation without permission. Incentiv chooses PoW not because it is old, but because it is the fairest and most inclusive way to secure an open network.
But we also recognize its flaws — so we fixed them.
The Problem with Traditional PoW
Classic PoW was not designed for modern economies.Its security budget is fixed, regardless of whether the network is empty or booming. During quiet periods it wastes energy; during peak usage it doesn’t increase security where it is most needed. Inflationary block rewards distort the token economy.
Miners earn the same amount whether the chain is providing value or not. Token holders are diluted continuously. The system has no responsiveness, no self-correction, and no relation to actual demand. In short: traditional PoW is static in a world that demands adaptability.
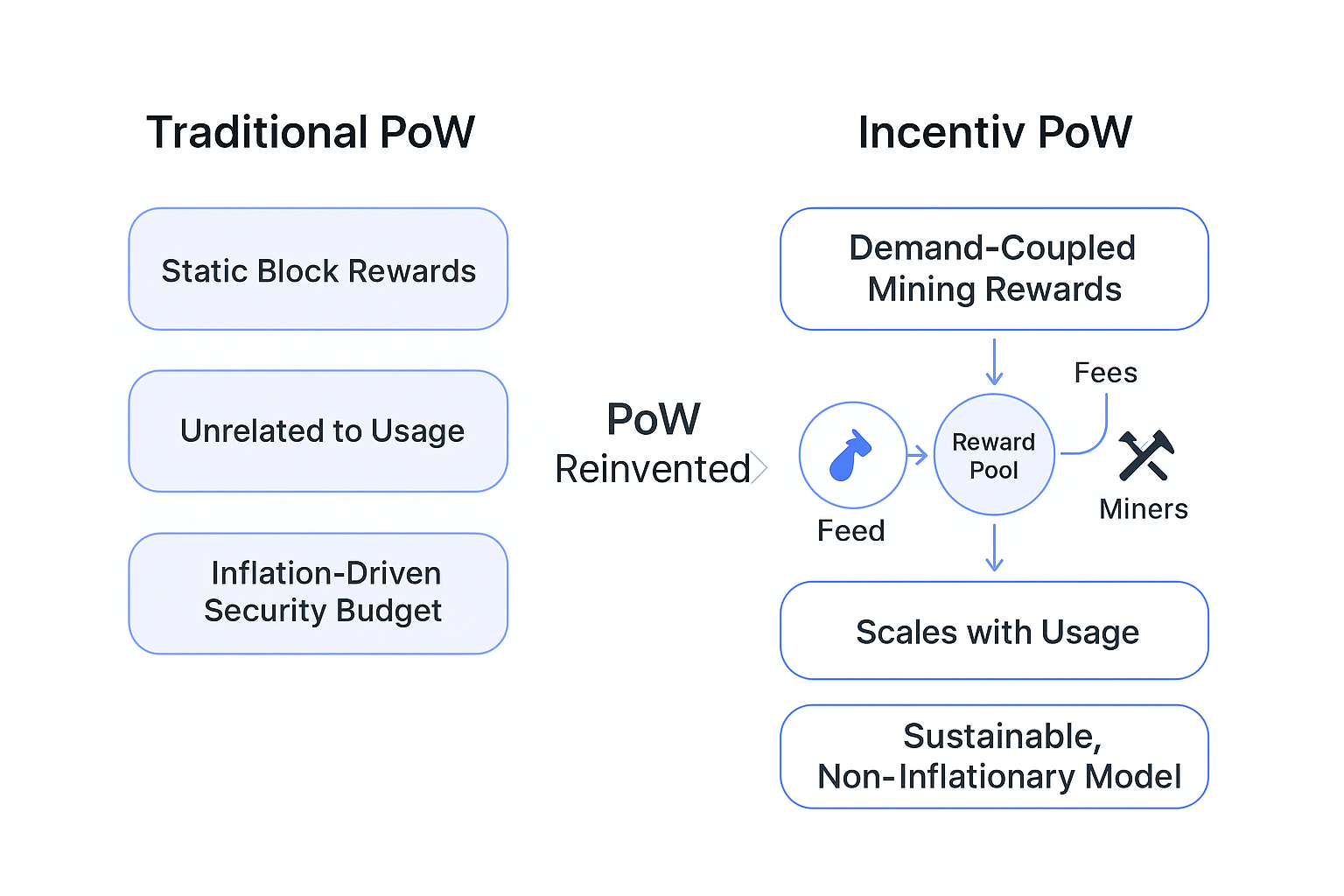
Our Solution: Demand-Coupled Proof-of-Work
Incentiv introduces a simple but transformative idea:the security budget should scale automatically with economic activity. When more users interact with the chain, when value flows increase, when applications thrive — Incentiv responds immediately. Mining rewards adjust based on:
- real transaction volume
- value-fee inflows
- total network usage
Low usage → smaller reward pool → reduced expenditure without compromising fairness The network breathes with demand.
Mining Designed for Humans
Incentiv uses an enhanced Ethash design — memory-hard, accessible, and GPU-friendly.This ensures mining remains decentralized and widely available. No closed validator sets, no hardware oligopolies. Anyone who contributes compute strengthens the shared infrastructure. This is how Incentiv maintains decentralization without sacrificing performance or inclusivity. Ethash Memory-Hard Mining
- GPU-friendly
- ASIC-resistant
- Secure and permissionless
- Keeps mining competitive instead of centralized
How It Works
Here’s how Incentiv’s consensus system operates end-to-end:- Miners compute Ethash proofs
GPUs perform memory-hard hashing to propose the next block. - Transactions enter block candidates
UserOperations and regular transactions are processed through the EVM, following Ethereum semantics. - Value fees flow into the shared reward pool
Each block collects transaction fees and value-based fees, contributing to the Incentiv+ reward system. - Demand adjusts the block reward dynamically
The protocol increases or decreases miner rewards based on real network activity and throughput. - Nodes validate and execute the block
Every node re-executes the EVM computation to confirm the correctness of the state transition. - Fork choice selects the chain with the most cumulative work
The longest-work chain is accepted, ensuring objectivity and resistance to manipulation. - Miners claim rewards proportional to both security contribution and network demand
Higher activity → larger reward pool → stronger economic alignment.
A Consensus Layer aligned with Contribution
By linking security, usage, and contribution, Incentiv transforms Proof-of-Work into a demand-driven, economically grounded engine. Miners aren’t just competing on hardware they’re securing real value and are rewarded in proportion to the ecosystem they help protect.This ensures sustainability, fairness, and long-term decentralization across the entire network.